With so many terrorist attacks around the globe, there may be a perception that the risk of terrorism is increasing. Whether this is the case or not is a hotly debated topic, but the nature of terrorism insurance is changing, even if the threat isn’t.
These changes in perceived risk and associated loss can be difficult to account for when considering new business. A combination of qualitative reporting and quantitative analysis is needed to provide insight into the multifaceted nature of terrorism risk.
Qualitative reporting can provide a national-level assessment of terrorism risk via the monitoring of three characteristics:
- An overview of the intensity and threat of known terrorist groups
- The impact of historical events
- Counterterrorism capabilities including security forces and policies
Quantitative means can enhance the overall view of risk through:
- Accumulation analyses of the current level of exposure in an area
- Loss assessments via deterministic scenarios
This blog discusses both qualitative and quantitative means of terrorism risk management using solutions from Verisk Maplecroft and AIR Worldwide.
Identifying and Understanding Terrorism Risks
Databases containing details of historical terrorist incidents and risk indexes derived from them are vital to understanding the evolving nature of terrorism risk. However, it is also crucial to have an assessment of the terrorism threat level and a view of counterterrorism capabilities.
Verisk Maplecroft’s Terrorism Incident Database, combined with its suite of terrorism indexes (updated quarterly), provides underwriters with analytics to understand the current threat to exposures and how that threat evolves over time.
The indexes cover 198 countries worldwide at national and subnational levels. The Terrorism Incident Database contains more than 130,000 incidents from 2004 to the present. Each incident record contains a narrative alongside up to 20 individual data points, including weapon types, perpetrator groups, casualty profiles, details of damage to physical assets, and the most precise geotag possible.
Verisk Maplecroft’s Terrorism Intensity Index assesses the magnitude and frequency of terror incidents based on analysis of one year’s worth of highly granular data (1-km2 resolution) at the subnational level. The History of Terrorism Index assesses the frequency and intensity of reported terrorism events from 2010–2015. By combining geotags for events from the Terrorist Incident Database with data from the Terrorism Intensity and History of Terrorism Indexes, underwriters can instantly quantify terrorism intensity on a 0–10 scale for any location worldwide.
In addition, Verisk Maplecroft’s Access an Analyst service taps the combined knowledge of political risk experts in more than 40 countries to offer qualitative assessments of the security risks posed to a particular region.
Terrorism Risk Management
Once an understanding of the terrorism landscape has been gained, analyses using AIR’s Touchstone® platform can be used to examine potential fiscal impacts. For risks located outside the U.S.,1 three methods can be combined to provide a comprehensive view of terrorism risk; these can be done at the individual account or portfolio level.
1) Ring-Based Analyses: Identifying the Point of Maximum Exposure
The point of maximum exposure within a portfolio can be identified using ring-based analyses and its exposed limit can be calculated for given radii. The Dynamic Ring Analysis functionality in Touchstone—as explained in this video—allows users to find the point at which a ring of a given size covers the maximum exposure concentration in their portfolios, pinpointing the area most vulnerable to a single terrorism event. This location can be cross-referenced with the risk profile developed by Verisk Maplecroft to ensure that a portfolio is not overly exposed to risk.
2) Accumulation Using Verisk Maplecroft’s Terrorism Intensity Index
These metrics can be used to compare the relative terrorism risk between accounts or portfolios. A real strength of Verisk Maplecroft is the suite of terrorism indexes across different themes. When considering the threat of terrorism, these indexes are developed further to produce a subnational terrorism risk map that details the risk index to a 1-km2 resolution (Figure 1).
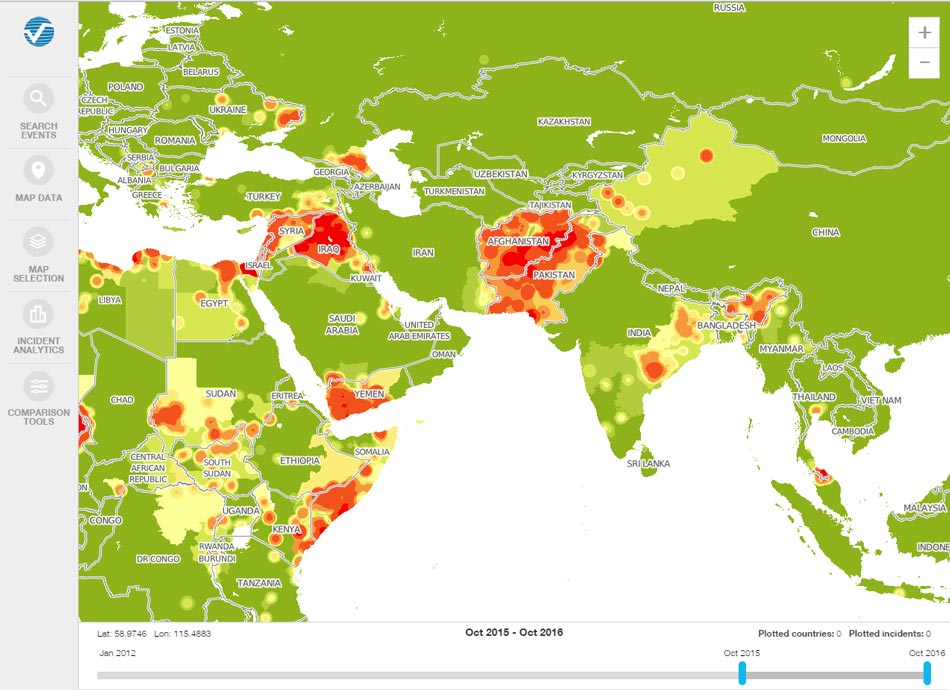
AIR has created a hazard layer from this map for use within the Geospatial Module of Touchstone. This allows users to analyze their exposure and identify exposed limits by risk band so that the concentration of exposure in a high risk area can be prevented, thus enabling the risk-based selection of contracts.
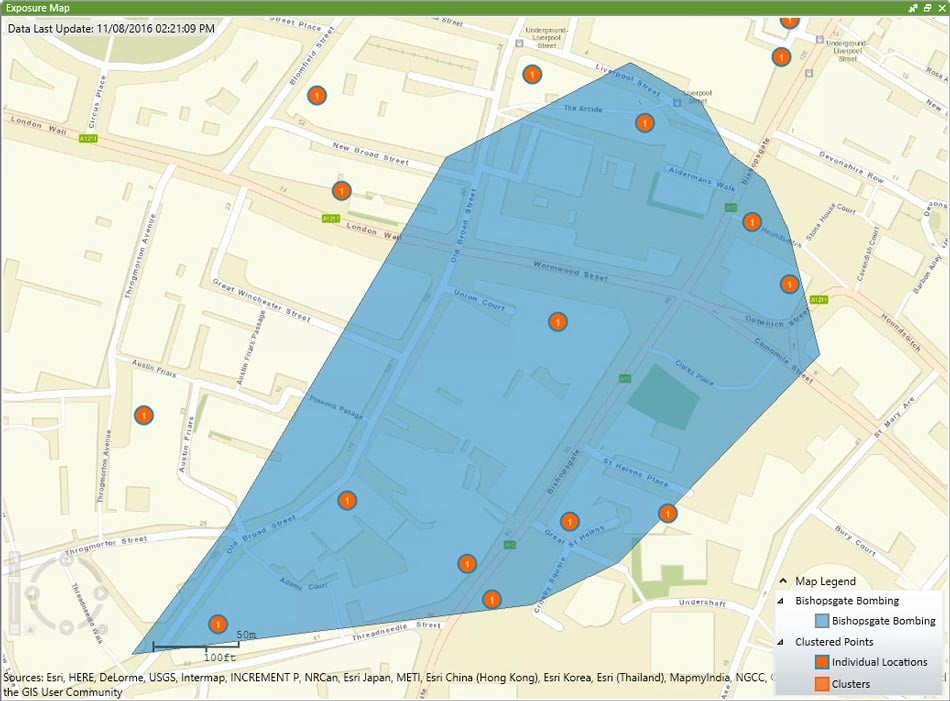
Another accumulation method, little used due to lack of available data, can still give insights into what would happen if historic attacks occurred today. Instead of being ring-based, this method uses accumulation of exposure within historical blast footprints, such as the 1993 Bishopsgate bombing in London. With improved data processing technology, historical images can be geotagged and used to create footprints on which to accumulate exposure; such work has been done by some organizations from which information is available (Figure 2).
3) Deterministic Loss Analysis
The third method is to calculate the potential loss if an attack were to actually occur. With Touchstone 4.0 (released June 2016), AIR provided the opportunity to run deterministic loss analyses for terrorism events in 27 countries around the globe (Figure 3). Deterministic analysis estimates losses (not exposed limits) from a blast of a defined tonnage of TNT centered at a specified location. These analyses use continuous physics-based blast attenuation functions and engineering expertise to estimate damage and loss within physically realistic footprints. Three primary pieces of information are used in a deterministic analysis: the urban density of the region where the blast is simulated; the tonnage of the weapon being used; and the vulnerability of the structure to overpressure.
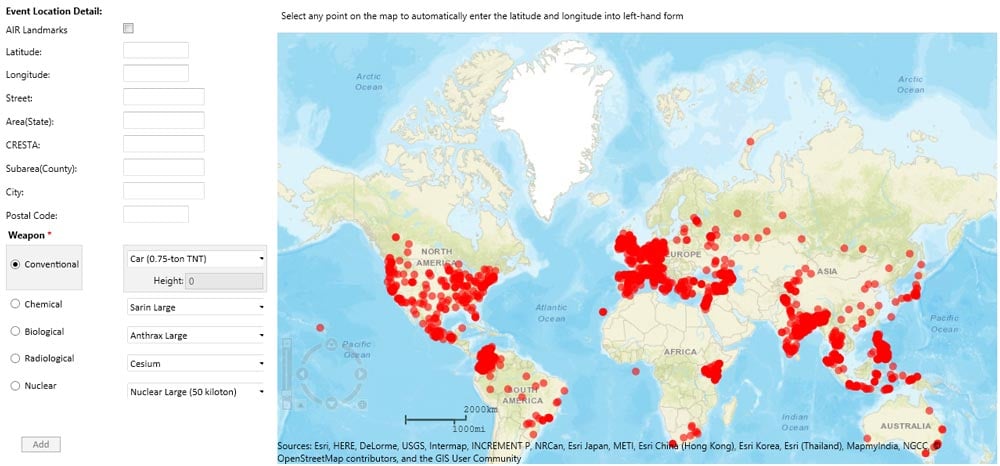
Using an Urban Density Index for these 27 countries, the severity of damage to a property from a variety of different devices ranging from a portable backpack bomb to a large truck bomb similar to that used in the Bishopsgate bombing can be simulated. The functions defining the vulnerability of structures to a blast have been developed like the vulnerability functions for other hazards. They have been fine-tuned using historical data and incorporate research by organizations such as the Department of Defence.
The reports and focused insights provided by Verisk Maplecroft allow risk professionals to understand the terrorism threat to their exposure on a regional and subregional basis. These insights can then be enhanced using Touchstone to consider the potential financial impacts within a threat band and to identify the point of maximum exposure within a ring. This financial view of the risk can be refined by using AIR’s Terrorism Model to consider estimated losses if a potential attack were to occur. Using a combination of the insights obtained through Verisk Maplecroft and Touchstone, a comprehensive view of terrorism risk can be quickly and easily achieved.
This post was published previously in CatIQ’s blog. Jonny Green will be speaking on nuclear modeling at the PONI 2017 Capstone Conference on March 16.
1 For exposure based within the U.S., licensees can also use AIR’s probabilistic terrorism model to assess risks using a 500,000-year stochastic catalog of events.